[VulnHub] - Jarbas: 1 Walkthrough
~ Spoiler Alert ~
Recently I did Jarbas from Vulnhub and below is my walkthrough for this machine.
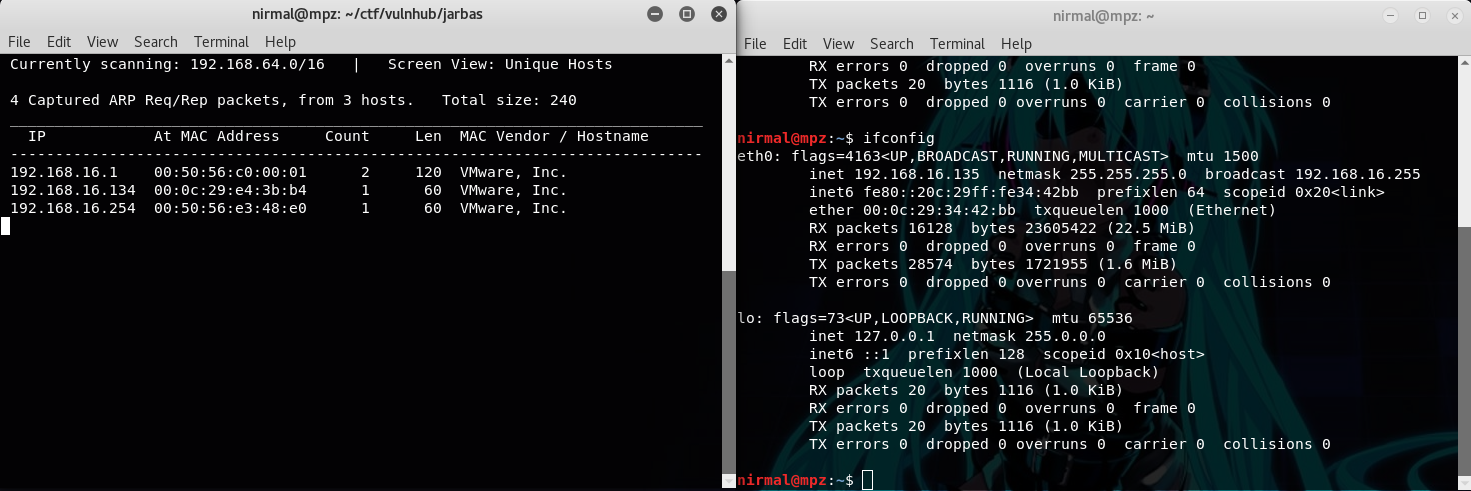
Firstly, to obtain the IP address of the target machine, I used netdiscover. My kali machine booted later than the target machine, so obviously Jarbas machine's IP is 192.168.16.134
A quick port scan on the IP address revealed some open ports like 22 (SSH), 80 & 8080 (HTTP), 3306 (mysql).
No SSH creds were initially provided and mysql also didn't allow to access remotely so I skipped port 22 and 3306 and moved towards the port 80. Homepage for port 80 looks something like below.
In the machine's description, the author has mentioned that this machine (Jarbas) is a tribute to a Brazilian Search engine of the 90's. The homepage of the machine also displays a static page copied from wayback machine of the same search engine jarbas.com.br. Since it's a static page directly copied from wayback machine, there's nothing interesting so I moved to port 8080. A jenkins instance was running on this port which had authentication :(
I tried some common creds like admin:admin, jenkins:jenkins, jenkins:jenkins123 etc. but none worked so I thought to visit this port later and went back to port 80 again. There was no sensitive info/hint in the source code too so I started bruting for dirs/files with gobuster and a dirbuster wordlist.
While bruteforcing for dirs/files (files with html & php extensions), I found this access.html file. Viewing this HTML file on browser, I got some creds with MD5 hashes.
I copied these hashes to hashkiller and fortunately 3/3 hashes were cracked.
Now we have these usernames and plaintext passwords so I tried to login to SSH but none of these worked so I tried these creds on jenkins instance running on port 8080. Luckily eder's credentials worked and I got logged into jenkins.
If we get access to jenkins instance, we can execute arbitrary commands on the server from Script Console and obtain a shell too. To verify it, I executed uname -a and got kernel info.
As /tmp dir is writable for anyone, I wrote a python oneliner reverse shell and saved at /tmp/rev.py.
For more details on exploiting jenkins instance check this out.
On executing this python script from /tmp directory, I got a reverse shell to my local machine and I also upgraded this netcat shell to a fully interactive TTY shell.
I did some basic enumeration manually but didn't find any clue which could help me to escalate to another user/root. So, I started a python server on my local machine and curl'ed linenum.sh; this script helps a lot in escalating privileges.
While going through the output of this script, I found this crontab content fishy.
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
which means CleaningScript.sh located at /etc/script is being run every 5mins as ROOT!
If we read this CleaningScript.sh script, we can see it deletes httpd's access log and also it is writable by anyone. I comment'ed this rm -rf line and replaced it with a simple one liner reverse shell payload from pentestmonkey and started a netcat listener on port 12345.
After waiting for few minutes, the script got executed as cronjob and I got a netcat session as root :D
uid=0(root) gid=0(root) groups=0(root) Mission accomplished.
I hope you enjoyed this walkthrough as much as I did when escalating to root and writing about it :)
EOBlog.
Recently I did Jarbas from Vulnhub and below is my walkthrough for this machine.
Firstly, to obtain the IP address of the target machine, I used netdiscover. My kali machine booted later than the target machine, so obviously Jarbas machine's IP is 192.168.16.134
A quick port scan on the IP address revealed some open ports like 22 (SSH), 80 & 8080 (HTTP), 3306 (mysql).
No SSH creds were initially provided and mysql also didn't allow to access remotely so I skipped port 22 and 3306 and moved towards the port 80. Homepage for port 80 looks something like below.
In the machine's description, the author has mentioned that this machine (Jarbas) is a tribute to a Brazilian Search engine of the 90's. The homepage of the machine also displays a static page copied from wayback machine of the same search engine jarbas.com.br. Since it's a static page directly copied from wayback machine, there's nothing interesting so I moved to port 8080. A jenkins instance was running on this port which had authentication :(
I tried some common creds like admin:admin, jenkins:jenkins, jenkins:jenkins123 etc. but none worked so I thought to visit this port later and went back to port 80 again. There was no sensitive info/hint in the source code too so I started bruting for dirs/files with gobuster and a dirbuster wordlist.
While bruteforcing for dirs/files (files with html & php extensions), I found this access.html file. Viewing this HTML file on browser, I got some creds with MD5 hashes.
I copied these hashes to hashkiller and fortunately 3/3 hashes were cracked.
Now we have these usernames and plaintext passwords so I tried to login to SSH but none of these worked so I tried these creds on jenkins instance running on port 8080. Luckily eder's credentials worked and I got logged into jenkins.
If we get access to jenkins instance, we can execute arbitrary commands on the server from Script Console and obtain a shell too. To verify it, I executed uname -a and got kernel info.
As /tmp dir is writable for anyone, I wrote a python oneliner reverse shell and saved at /tmp/rev.py.
For more details on exploiting jenkins instance check this out.
On executing this python script from /tmp directory, I got a reverse shell to my local machine and I also upgraded this netcat shell to a fully interactive TTY shell.
I did some basic enumeration manually but didn't find any clue which could help me to escalate to another user/root. So, I started a python server on my local machine and curl'ed linenum.sh; this script helps a lot in escalating privileges.
While going through the output of this script, I found this crontab content fishy.
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
which means CleaningScript.sh located at /etc/script is being run every 5mins as ROOT!
If we read this CleaningScript.sh script, we can see it deletes httpd's access log and also it is writable by anyone. I comment'ed this rm -rf line and replaced it with a simple one liner reverse shell payload from pentestmonkey and started a netcat listener on port 12345.
After waiting for few minutes, the script got executed as cronjob and I got a netcat session as root :D
uid=0(root) gid=0(root) groups=0(root) Mission accomplished.
I hope you enjoyed this walkthrough as much as I did when escalating to root and writing about it :)
EOBlog.

















Hi! I've just added you writeup into Jarbas page. tiagotavares.io.
ReplyDeleteRegards!
Tiago