Expanding the attack surface with Shodan's lesser known filter
I have been using Shodan extensively for bug bounty hunting lately and I found some neat tricks to expand the attack surface of the given target. There are many blogs and tutorials on "Shodan Recon" and most of them talk about the same filters - ssl, ssl.cert.subject.cn, org, ip, hostname, etc. but I have not seen anyone talk about this filter - all. So, I won't talk much about the basics of shodan and directly jump to the topic.
Shodan's regular search bar (without any filter) is not consistent and when you search for a keyword, it only looks for the "keyword" in https://www.shodan.io/host/<ip> BUT shodan's raw data (https://www.shodan.io/host/<ip>/raw) contains much more information or what I like to call it as "references" about the target. To find those references and juicy hosts, this "all" filter is very handy. I have been using this filter a lot and it has found many hosts that no other filter could find. The usage is pretty simple as well - all:"InternalDomain", all:"SomethingInternalKeyword".. and so on.
The results might contain false positives or assets a company may not own but they can be reduced by combining with other filters. For example, let's say my target is Grab and I'm looking for assets owned by them. What I will do is, use this filter as all:grab.
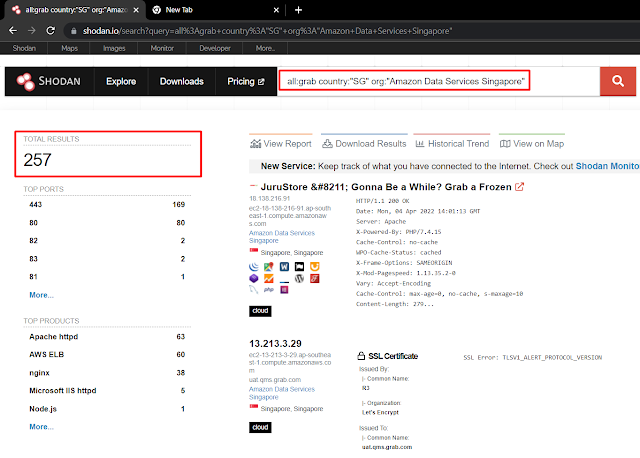
25k hosts hmmmm. Let's reduce the numbers! Grab is based in Southeast Asia (mostly Singapore) and their infra is mostly in AWS/Azure. Using this same information, we can craft another search query - all:grab country:"SG" org:"Amazon Data Services Singapore"
25k hosts reduced to 257. Check each result one by one, you will be surprised by the information that you can find about your target ;)


Comments
Post a Comment